Nothing to say about google. You can search google for a result even from your linux command line.
curl -A Mozilla http://www.google.com/search?q=Linux |html2text -width 80
You need to install CURL and HTML2TEXT in your box.
apt-get install curl html2text (Debian / Ubuntu)
yum install curl html2text (Fedora / Centos / RHEL)
Enjoy ....
Aug 17, 2009
Update Twitter from a Linux Shell
Everybody knows now about TWITTER. It is a free social networking and micro-blogging service that enables its users to send and read messages known as tweets. Tweets are text-based posts of up to 140 characters displayed on the author's profile page and delivered to the author's subscribers who are known as followers. Senders can restrict delivery to those in their circle of friends or, by default, allow open access. Users can send and receive tweets via the Twitter website, Short Message Service (SMS) or external applications. While the service costs nothing to use, accessing it through SMS may incur phone service provider fees.
There is a lot of APIs available to update twitter now like TwitterFox (Firefox Addon) TweetDeck. But now how can I update twitter from my Linux terminal ? Here follows the answer. This is simple using CURL.
There is a lot of APIs available to update twitter now like TwitterFox (Firefox Addon) TweetDeck. But now how can I update twitter from my Linux terminal ? Here follows the answer. This is simple using CURL.
curl -u user:password -d status=”Your status message” http://twitter.com/statuses/update.xml
Wher user is your twitter username and password is your twitter password .
If curl is not installed do the following
apt-get install curl (Debian / Ubuntu)
yum install curl (Fedora / RHEL / Centos)
So keep in touch with twitter if you are in Datacentre .....
Jun 18, 2009
Apache Error - No space left on device: Couldn't create accept lock or Cannot create SSLMutex
Some times you people may face this following error in your Apache Server. The error is as follows while trying to restart.after a configuration changes or something like that
[emerg] (28)No space left on device: Couldn't create accept lock
OR
[crit] (28)No space left on device: mod_rewrite: could not create rewrite_log_lock Configuration Failed
OR
[Wed Dec 07 00:00:09 2005] [error] (28)No space left on device: Cannot create SSLMutex
This is happened due to someking of memory leaking. Normally people do the following to fix this.
1.Checking the harddisk space usage
2.To explicetely different Lockfiles using the LockFile-directive
3.non-default AcceptMutex (flock) which then solved the acceptlock-issue and ended in the rewrite_log_lock-issue.
4.Reboot
The fourth option will only work,because this is due to the following reason
There were myriads of semaphore-arrays left, owned by my apache-user. Removing this semaphores immediately solved the problem
Do the following as ROOT
[root@apache.org] ipcs -s | grep apache | perl -e 'while () { @a=split(/\s+/); print `ipcrm sem $a[1]`}' -- (If You Love Perl)
[root@apache.org] ipcs -s | grep apache | awk ' { print $2 } ' | xargs ipcrm sem (If you Love Sh)
Have a great Day with Apache !!!
May 23, 2009
Apache Real Time monitoring APACHETOP
Apache top is another tool for apache real time monitoring. This is just like the TOP command in *nix based systems. Here this can show a lot of informations from the Apache Web Server.
[root@apache.org]mkdir -p /opt/src
[root@apache.org]cd /opt/src
[root@apache.org]wget http://www.webta.org/apachetop/apachetop-0.12.6.tar.gz
[root@apache.org]tar -zxf apachetop-0.12.6.tar.gz
[root@apache.org]cd apachetop-0.12.6
[root@apache.org]./configure --with-logfile=/var/log/httpd/access_log
[root@apache.org]make
[root@apache.org]make install
OK,Lets trigger it....
[root@apache.org] apachetop
Following Screenshot says it all. This was taken from my local test machine.
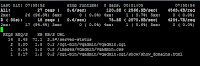
Try apachetop --help for more available switches
[root@apache.org]mkdir -p /opt/src
[root@apache.org]cd /opt/src
[root@apache.org]wget http://www.webta.org/apachetop/apachetop-0.12.6.tar.gz
[root@apache.org]tar -zxf apachetop-0.12.6.tar.gz
[root@apache.org]cd apachetop-0.12.6
[root@apache.org]./configure --with-logfile=/var/log/httpd/access_log
[root@apache.org]make
[root@apache.org]make install
OK,Lets trigger it....
[root@apache.org] apachetop
Following Screenshot says it all. This was taken from my local test machine.

Try apachetop --help for more available switches
Apache RealTime Monitoring MOD_STATUS
There is number of tools available to monitor apache in realtime. Like Nagios,Cacti etc. But those tools are little difficult to configure for the first time (Experts Please excuse :-) ). Here I would like to introduce couple of simple tools which help the Webserver admin to monitor his Apache webserver in real time through Web and Console.
Mod_Status
Status Module is a builtin module for apache for a default installation. First checkout whether this module is compiled with your Apache.
[root@apache.org] cat /etc/httpd/conf/httpd.conf | grep status_module
LoadModule status_module modules/mod_status.so
Make sure this line was not comment out. OK,Lets take the backup of your current configuration file
[root@apache.org]cp /etc/httpd/conf/httpd.conf /etc/httpd/conf/httpd.conf_backup
[root@apache.org]vim /etc/httpd/conf/httpd.conf
Goto Last Line and Paste the following
SetHandler server-status
Order Deny,Allow
Allow from all
<\Location >
Search for the Line "ExtendedStatus". Normally this line is commented out. Uncomment it.
Save and Exit
Take your browser. http://your.domain.com/server-status
Take a look at the values,Its Realtime values from the Apache. To view this page continuously,I mean refreshing automatically
http://your.domain.com/server-status?refresh=N
(This N is any number).
May 18, 2009
Update notification through email RHEL / Centos
As everybody know,the system should be update. So an administrator should be vigilant on the new updates and patches from the vendor. But how do we know there is a patch available in the remote server. Here a way to get notified when an update is available.
#vim /etc/yum/yum-updatesd.conf
#vim /etc/yum/yum-updatesd.conf
[main]
# how often to check for new updates (in seconds)
run_interval = 3600
# how often to allow checking on request (in seconds)
updaterefresh = 600
# how to send notifications (valid: dbus, email, syslog)
emit_via = email
# who to send the email
email_to = admin@adminguru.co.nr
# who send the notifications
email_from = updates@backup.server.com
#
# should we listen via dbus to give out update information/check for
# new updates
dbus_listener = yes
# automatically install updates
do_update = no
# automatically download updates
do_download = no
# automatically download deps of updates
do_download_deps = no
Save and Exit
Restart the Yum updater
#/etc/init.d/yum-updatesd restart
You will be notified when an update is available. Sample Email is as follows.
Hi,
This is the automatic update system on server.backup.com.
There are 2 package updates available. Please run the system updater.
Packages available for update:
kernel-2.6.18-92.el5
kopete
Thank You,
Your Computer
Block Coutry wise traffic using Iptables.
Some countries are blacklisted in ecommerce area due to spam flooding and DoS attacks. Its not difficult to find the root of an IP address. So the following script will block country based traffic in to your web server. The data will be updated in every day through a cronjob.
You need to visit this SITE to download the zone file for which country you need to block.
#mkdir -p /opt/scripts
#vim /opt/scripts/ip_country_deny.sh
Copy Paste the following
Setup a crontab for working in every day
#vim /etc/crontab
Add the following at the end of the file
03 03 * * * root /opt/scripts/ip_country_deny.sh
To start the script immediately
#/opt/scripts/ip_country_deny.sh
#iptable -L -n -v
Check out the wonderful output....
You need to visit this SITE to download the zone file for which country you need to block.
#mkdir -p /opt/scripts
#vim /opt/scripts/ip_country_deny.sh
Copy Paste the following
#!/bin/bashSave and Exit
### Block all traffic from AFGHANISTAN (af) and CHINA (CN). Use ISO code ###
ISO="af cn"
### Set PATH ###
IPT=/sbin/iptables
WGET=/usr/bin/wget
EGREP=/bin/egrep
### No editing below ###
SPAMLIST="countrydrop"
ZONEROOT="/root/iptables"
DLROOT="http://www.ipdeny.com/ipblocks/data/countries"
cleanOldRules(){
$IPT -F
$IPT -X
$IPT -t nat -F
$IPT -t nat -X
$IPT -t mangle -F
$IPT -t mangle -X
$IPT -P INPUT ACCEPT
$IPT -P OUTPUT ACCEPT
$IPT -P FORWARD ACCEPT
}
# create a dir
[ ! -d $ZONEROOT ] && /bin/mkdir -p $ZONEROOT
# clean old rules
cleanOldRules
# create a new iptables list
$IPT -N $SPAMLIST
for c in $ISO
do
# local zone file
tDB=$ZONEROOT/$c.zone
# get fresh zone file
$WGET -O $tDB $DLROOT/$c.zone
# country specific log message
SPAMDROPMSG="$c Country Drop"
# get
BADIPS=$(egrep -v "^#|^$" $tDB)
for ipblock in $BADIPS
do
$IPT -A $SPAMLIST -s $ipblock -j LOG --log-prefix "$SPAMDROPMSG"
$IPT -A $SPAMLIST -s $ipblock -j DROP
done
done
# Drop everything
$IPT -I INPUT -j $SPAMLIST
$IPT -I OUTPUT -j $SPAMLIST
$IPT -I FORWARD -j $SPAMLIST
# call your other iptable script
# /path/to/other/iptables.sh
exit 0
#Script Ends Here....
Setup a crontab for working in every day
#vim /etc/crontab
Add the following at the end of the file
03 03 * * * root /opt/scripts/ip_country_deny.sh
To start the script immediately
#/opt/scripts/ip_country_deny.sh
#iptable -L -n -v
Check out the wonderful output....
Disable USB in Grub
Now a days USB storage devices are common in the industry. This is very halmful in any unsecured network. Because this devices are considered to be the virus spreading agents. In corporates USB media is prevented because of above said reasons. So here a small tip to prevent USB storage in Linux machines through GRUB.
Scenario
OS : Debian / Ubuntu
Open the Grub configuration file
#vi /boot/grub/menu.lst
Add "nousb" at the end of the Kernel Line. Like the following
kernel /vmlinuz-2.6.18-128.1.1.el5 ro root=LABEL=/ console=tty0 console=ttyS1,19200n8 nousb
Secure GRUB with a strong Password !!!
#/sbin/shutdown -r now
So nobody can use USB storage unless you allowed to do so.
May 17, 2009
Adding a VLAN in CISCO 2900
Creating a Virtual Lan is an advanced job in the case of networking. This needs experience in networking,Switching etc. But here i am stating how to add a new VLAN in the CISCO 2900 XL.
Assumptions
1.You have a basic knowledge in networking
2.You have the administrator access to switch
3.You should be aware on what you are doing !!!
CISCO2900>switchport mod access
CISCO2900>switchport mod access vlan5
CISCO2900>conf t
CISCO2900>int Fast 0/31
CISCO2900>description To Marketing LAN
CISCO2900>write
DONE.
Assumptions
1.You have a basic knowledge in networking
2.You have the administrator access to switch
3.You should be aware on what you are doing !!!
CISCO2900>switchport mod access
CISCO2900>switchport mod access vlan5
CISCO2900>conf t
CISCO2900>int Fast 0/31
CISCO2900>description To Marketing LAN
CISCO2900>write
DONE.
May 16, 2009
Qmail Tips & Tricks.
qmail is a mail transfer agent that runs on Unix. It was written, starting December 1995, by Daniel J. Bernstein as a more secure replacement for the popular Sendmail program. qmail's source code is released to the public domain, making qmail free software. Most Popular email services like Yahoo,Gmail are using qmail for their mail traffic. Here I am pasting some qmail tips,which helped me to override when I was blackout with my Qmail Box.
qmailctl - This command will show you a lot of information about your qmail server.
[root@mail.admin.org] qmailctl stat
/service/qmail-send: up (pid 3030) 30 seconds
/service/qmail-send/log: up (pid 3025) 30 seconds
/service/qmail-smtpd: up (pid 3028) 30 seconds
/service/qmail-smtpd/log: up (pid 3029) 30 seconds
/service/qmail-pop3d: up (pid 3026) 30 seconds
/service/qmail-pop3d/log: up (pid 3027) 30 seconds
messages in queue: 0
messages in queue but not yet preprocessed: 0
The above output means your Qmail server is Ready to deliver / receive messages. The seconds figure should be same,for a clean server.
[root@mail.admin.org]qmailctl queue
messages in queue: 0
messages in queue but not yet preprocessed: 0
This will shows the list of mails which were not delivered in the server.
[root@mail.admin.org]qmailctl queue | wc -l
Which will give the number of mails in the queue.
[root@mail.admin.org]qmailctl start
Starts mail service (smtp connection accepted, mail can go out)
[root@mail.admin.org]qmailctl stop
Stops mail service (smtp connections refused, nothing goes out).
[root@mail.admin.org]qmailctl pause
Temporarily stops mail service (connections accepted, nothing leaves).
To block a sender or entire domain to your Qmail Box. Because some times you need to block a user or entire domain from outside world to reach to your qmail
[root@mail.admin.org] vi /var/qmail/control/badmailfrom
Inside the " badmailfrom " file, the syntax might look something like this:
spam@spammerhell.org
@spammerhell.org
What do the above lines do?
The entry for "spam@spammerhell.org" would block all mail coming from "spam@spammerhell.org".
The entry for "@spammerhell.org" would block any and all mail coming from the domain "@spammerhell.org".
To be Continued....
Because Qmail Administration is an Ocean,I am just seeing it from the Shore. ..
May 11, 2009
Beautifying Nagios
Nagios is a popular open source computer system and network monitoring software application. It watches hosts and services, alerting users when things go wrong and again when they get better. Nagios, originally created under the name NetSaint, was written and is currently maintained by Ethan Galstad, along with a group of developers actively maintaining both official and unofficial plugins. Nagios was originally designed to run under Linux, but also runs well on other Unix variants. There is lot of plugins available in nagios for various purposes. But so far nothing found to beautify nagios from traditional look. Now there is a beautiful theme available
to beautify the nagios. This will give you a new look for your monitoring master.Assumptions.
You have installed and setup Nagios for your network.
You are the Nagios Administrator.
You have installed and setup Nagios for your network.
You are the Nagios Administrator.
[nagios@server]# wget http://tomas.cat/blog/sites/default/files/nagios-nuvola-1.0.3.tar_.gz
[nagios@server]# tar zxvf nagios-nuvola-1.0.3.tar_.gz
[nagios@server]# cp -a nuvola/html/* /usr/share/nagios3/htdocs/
[nagios@server]# cp -a nuvola/html/stylesheets/* /etc/nagios3/stylesheets/.
Reload Nagios
[nagios@server]#/usr/local/nagios/bin/nagios -v /usr/local/nagios/etc/nagios.cfg
[nagios@server]# /etc/init.d/nagios reload
Check out......How beautiful ........
ScreenShots of my Nagios server after Makeup

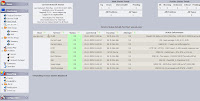
Apr 16, 2009
How to Find Server is Under DDOS
A denial-of-service attack (DoS attack) or distributed denial-of-service attack (DDoS attack) is an attempt to make a computer resource unavailable to its intended users. Although the means to carry out, motives for, and targets of a DoS attack may vary, it generally consists of the concerted efforts of a person or persons to prevent an Internet site or service from functioning efficiently or at all, temporarily or indefinitely. Perpetrators of DoS attacks typically target sites or services hosted on high-profile web servers such as banks, credit card payment gateways, and even root nameservers.
netstat -anp | grep "tcp\|udp" | awk {'print $5'} | cut -d: -f1 | uniq -c | sort -n
So what will be the output ?
1 0.0.0.0
1 208.80.152.2
1 208.80.152.2
1 208.80.152.3
1 209.85.135.103
1 209.85.135.113
1 74.125.43.113
2 208.80.152.2
2 208.80.152.3
2 208.80.152.3
3 0.0.0.0
3 208.80.152.2
Left column indicates the number of connection,from the IP address which shown in right column. This was taken from my local test machine. If you are under an attack,this number may vary. The number will be any number.
Apr 14, 2009
Manage your Server Farm with CapistranO
Capistrano is an open source tool for running scripts on multiple servers; its main use is deploying web applications. It automates the process of making a new version of an application available on one or more web servers, including supporting tasks such as changing databases. Capistrano is written in the Ruby language and is distributed using the RubyGems distribution channel. It is an outgrowth of the Ruby on Rails web application framework, but has also been used to deploy web applications written using other frameworks, including ones written in PHP. The usage on the bash command line is easy to learn. When used with the Ruby on Rails Framework many default Capistrano recipes can be used, e.g. to deploy current changes to the web application or roll back to the previous deployment state.
Installation
#apt-get install ruby1.8 ruby1.8-dev rubygems1.8 libruby-extras libruby1.8-extras
(Ubuntu / Debian)
#yum install ruby1.8 ruby1.8-dev rubygems1.8 libruby-extras libruby1.8-extras
(Centos / Redhat)
Check the Ruby Details
#ruby -v
ruby 1.8.7
OK,Lets move to install Capistrano Boy
#gem install -y capistrano echoe
Capistrano makes a few assumptions about your servers. In order to use Capistrano, you will need to comply with these assumptions:
- You are using SSH to access your remote machines. Telnet and FTP are not supported.
- Your remote servers have a POSIX-compatible shell installed. The shell must be called “sh” and must reside in the default system path.
- If you are using passwords to access your servers, they must all have the same password. Because this is not generally a good idea, the preferred way of accessing your
- servers is with a public key. Make sure you’ve got a good passphrase on your key.
We are going to trigger some examples here. So my remote servers are 192.168.1.12 and 192.168.1.13 (You can Add any number here).
In the following example we are going to check the uptime of above servers.
Copy paste the following code into a text editor (Vim,Emacs).
task :health, :hosts => "192.168.1.12" , "192.168.1.13" do
run "uptime"
end
Save the file with name "capfile" without any extension.
Wakeup the code
#cap health
I found that some times while you apply this command shell returned an error "Command not found",then do the following
#vi ~/.bashrc
Copy paste the following at the end of the File
export PATH=$PATH:/var/lib/gems/1.8/bin
Then rebuild the bashrc
# source ~/.bashrc
Then Re-run the command,If you are against a password access server,it will ask for the password,enter it,other wise the result will be like following
[192.168.1.12] executing command
[192.168.1.13] executing command
** [out :: 192.168.1.12] 11:30:55 up 27 days, 22:40, 0 users, load average: 0.01, 0.01, 0.00
** [out :: 192.168.1.12] 11:30:55 up 37 days, 08:40, 0 users, load average: 0.05, 0.01, 0.08
command finished
We Can Do any command by the above said method,I hope you will be happy if you have a critical update on all of your 100 servers ...
Is int it ?
Apr 12, 2009
Monitoring Disk Usage In Linux
One of the routine job of a Linux administrator to monitor the Disk space continuously. Normal people will write a simple script to check the disk space and report to system administrator through email. Good Idea,but here i am telling a new one which will continuously monitor your Disk and report if it cross a preset value. This will run as a cronjob.
#!/bin/bash
#Script for monitoring Disk Usage
#Author BipinDas,Arab Open University.
ADMIN="yourname@yourdomain.com"
# set alert level 80% is default
ALERT=80
df -H | grep -vE '^Filesystem|tmpfs|cdrom' | awk '{ print $5 " " $1 }' | while read output;
do
#echo $output
usep=$(echo $output | awk '{ print $1}' | cut -d'%' -f1 )
partition=$(echo $output | awk '{ print $2 }' )
if [ $usep -ge $ALERT ]; then
echo "Running out of space \"$partition ($usep%)\" on $(hostname) $(hostname -i) as on $(date)" |
mail -s "Alert: Almost out of disk space $usep " $ADMIN
fi
done
Save it as disk_monitor.sh in your scripts folder.
Open Crontab Editor
vi /etc/crontab
*/5 * * * * root /path/to/script/disk_monitor.sh
Perfect,This will frequently check your Disk and inform once it cross the limit.
#!/bin/bash
#Script for monitoring Disk Usage
#Author BipinDas,Arab Open University.
ADMIN="yourname@yourdomain.com"
# set alert level 80% is default
ALERT=80
df -H | grep -vE '^Filesystem|tmpfs|cdrom' | awk '{ print $5 " " $1 }' | while read output;
do
#echo $output
usep=$(echo $output | awk '{ print $1}' | cut -d'%' -f1 )
partition=$(echo $output | awk '{ print $2 }' )
if [ $usep -ge $ALERT ]; then
echo "Running out of space \"$partition ($usep%)\" on $(hostname) $(hostname -i) as on $(date)" |
mail -s "Alert: Almost out of disk space $usep " $ADMIN
fi
done
Save it as disk_monitor.sh in your scripts folder.
Open Crontab Editor
vi /etc/crontab
*/5 * * * * root /path/to/script/disk_monitor.sh
Perfect,This will frequently check your Disk and inform once it cross the limit.
Subscribe to:
Posts (Atom)